Question 1
Which statement best describes the Turbo ACL feature? (Choose all that apply)
A. The Turbo ACL feature processes ACLs into lookup tables for greater efficiency.
B. The Turbo ACL feature leads to increased latency, because the time it takes to match the packet is variable.
C. The Turbo ACL feature leads to reduced latency, because the time it takes to match the packet is fixed and consistent.
D. Turbo ACLs increase the CPU load by matching the packet to a predetermined list.
Answer: A C
Question 2
Which statement best describes configuring access control lists to control Telnet traffic destined to the router itself
A. The ACL must be applied to each vty line individually.
B. The ACL should be applied to all vty lines in the in direction to prevent an unwanted user from connecting to an unsecured port.
C. The ACL is applied to the Telnet port with the ip access-group command.
D. The ACL applied to the vty lines has no in or out option like ACL being applied to an interface.
Answer: B
Question 3
Which description is correct based on the exhibit and partial configuration?
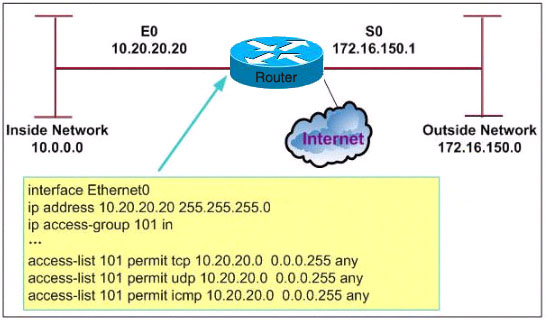 A. All traffic from network 10.0.0.0 will be permitted.
A. All traffic from network 10.0.0.0 will be permitted.
B. This ACL will prevent any host on the Internet from spoofing the inside network address as the source address for packets coming into the router from the Internet.
C. Access-list 101 will prevent address spoofing from interface E0.
D. All traffic destined for network 172.16.150.0 will be denied due to the implicit deny all.
Answer: C
Question 4
Examine the following options, which access list will permit HTTP traffic sourced from host 10.1.129.100 port 3030 destined to host 192.168.1.10
A. access-list 101 permit tcp 10.1.129.0 0.0.0.255 eq www 192.168.1.10 0.0.0.0 eq www
B. access-list 101 permit tcp 10.1.128.0 0.0.1.255 eq 3030 192.168.1.0 0.0.0.15 eq www
C. access-list 101 permit tcp host 192.168.1.10 eq 80 10.1.0.0 0.0.255.255 eq 3030
D. access-list 101 permit tcp any eq 3030
Answer: B
Question 5
Which three statements about applying access control lists to a Cisco router are true? (Choose three)
A. Place more specific ACL entries at the top of the ACL.
B. ACLs always search for the most specific entry before taking any filtering action.
C. Router-generated packets cannot be filtered by ACLs on the router.
D. Place generic ACL entries at the top of the ACL to filter general traffic and thereby reduce “noise” on the network.
E. If an access list is applied but is not configured, all traffic will pass.
Answer: A C E
Question 6
A standard access control list has been configured on a router and applied to interface Serial 0 in an outbound direction. No ACL is applied to Interface Serial 1 on the same router. What will happen when traffic being filtered by the access list does not match the configured ACL statements for Serial0?
A. The source IP address is checked, and, if a match is not found, traffic is routed out interface Serial 1.
B. The resulting action is determined by the destination IP address.
C. The resulting action is determined by the destination IP address and port number.
D. The traffic is dropped.
Answer: D
Question 7
Which location will be recommended for extended or extended named ACLs?
A. a location as close to the destination traffic as possible
B. an intermediate location to filter as much traffic as possible
C. when using the established keyword, a location close to the destination point to ensure that return traffic is allowed
D. a location as dose to the source traffic as possible
Answer: D
Which statement best describes the Turbo ACL feature? (Choose all that apply)
A. The Turbo ACL feature processes ACLs into lookup tables for greater efficiency.
B. The Turbo ACL feature leads to increased latency, because the time it takes to match the packet is variable.
C. The Turbo ACL feature leads to reduced latency, because the time it takes to match the packet is fixed and consistent.
D. Turbo ACLs increase the CPU load by matching the packet to a predetermined list.
Answer: A C
Question 2
Which statement best describes configuring access control lists to control Telnet traffic destined to the router itself
A. The ACL must be applied to each vty line individually.
B. The ACL should be applied to all vty lines in the in direction to prevent an unwanted user from connecting to an unsecured port.
C. The ACL is applied to the Telnet port with the ip access-group command.
D. The ACL applied to the vty lines has no in or out option like ACL being applied to an interface.
Answer: B
Question 3
Which description is correct based on the exhibit and partial configuration?

B. This ACL will prevent any host on the Internet from spoofing the inside network address as the source address for packets coming into the router from the Internet.
C. Access-list 101 will prevent address spoofing from interface E0.
D. All traffic destined for network 172.16.150.0 will be denied due to the implicit deny all.
Answer: C
Question 4
Examine the following options, which access list will permit HTTP traffic sourced from host 10.1.129.100 port 3030 destined to host 192.168.1.10
A. access-list 101 permit tcp 10.1.129.0 0.0.0.255 eq www 192.168.1.10 0.0.0.0 eq www
B. access-list 101 permit tcp 10.1.128.0 0.0.1.255 eq 3030 192.168.1.0 0.0.0.15 eq www
C. access-list 101 permit tcp host 192.168.1.10 eq 80 10.1.0.0 0.0.255.255 eq 3030
D. access-list 101 permit tcp any eq 3030
Answer: B
Question 5
Which three statements about applying access control lists to a Cisco router are true? (Choose three)
A. Place more specific ACL entries at the top of the ACL.
B. ACLs always search for the most specific entry before taking any filtering action.
C. Router-generated packets cannot be filtered by ACLs on the router.
D. Place generic ACL entries at the top of the ACL to filter general traffic and thereby reduce “noise” on the network.
E. If an access list is applied but is not configured, all traffic will pass.
Answer: A C E
Question 6
A standard access control list has been configured on a router and applied to interface Serial 0 in an outbound direction. No ACL is applied to Interface Serial 1 on the same router. What will happen when traffic being filtered by the access list does not match the configured ACL statements for Serial0?
A. The source IP address is checked, and, if a match is not found, traffic is routed out interface Serial 1.
B. The resulting action is determined by the destination IP address.
C. The resulting action is determined by the destination IP address and port number.
D. The traffic is dropped.
Answer: D
Question 7
Which location will be recommended for extended or extended named ACLs?
A. a location as close to the destination traffic as possible
B. an intermediate location to filter as much traffic as possible
C. when using the established keyword, a location close to the destination point to ensure that return traffic is allowed
D. a location as dose to the source traffic as possible
Answer: D
